Role Management in GitFlic
In GitFlic, you can manage the roles of other users whom you add to your project or team/company. Roles are arranged in order of increasing permissions and enable more efficient group collaboration. You can configure access to each project by assigning roles, giving people access to the features and tasks they need.
Available Basic Roles
In order of increasing permissions, the roles for a project are as follows:
- Guest
- Reporter
- Developer
- Administrator
- Owner
You can learn more about the permissions for each role here.
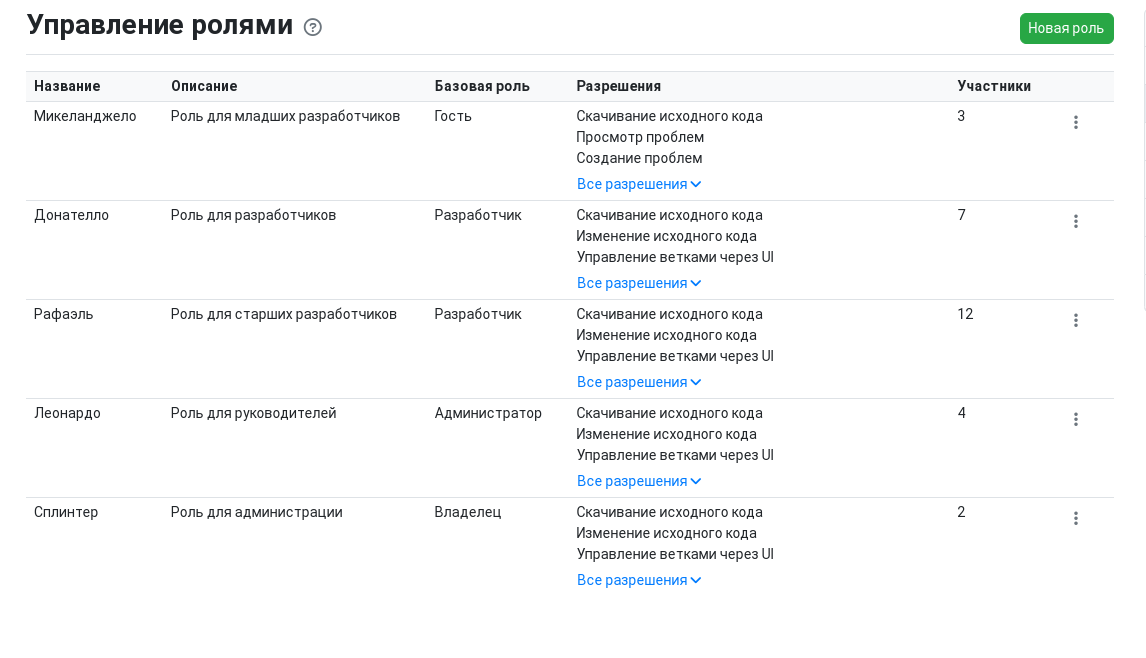
Custom Roles
This feature is available in the Enterprise, Atlas version and on gitflic.ru
For more flexible project access management, GitFlic allows you to create custom roles. RBAC (Role-Based Access Control) lets you configure roles with a unique set of permissions.
Creating Custom Roles
You can create custom roles in two ways:
- In company settings. This way, the created role can only be assigned to members of company projects.
- In the service-wide settings. In this case, a custom role can be assigned to any project member in the service.
Creating roles at the service-wide level is available only in the Enterprise version.
On gitflic.ru, there is a limit of 10 roles per company.
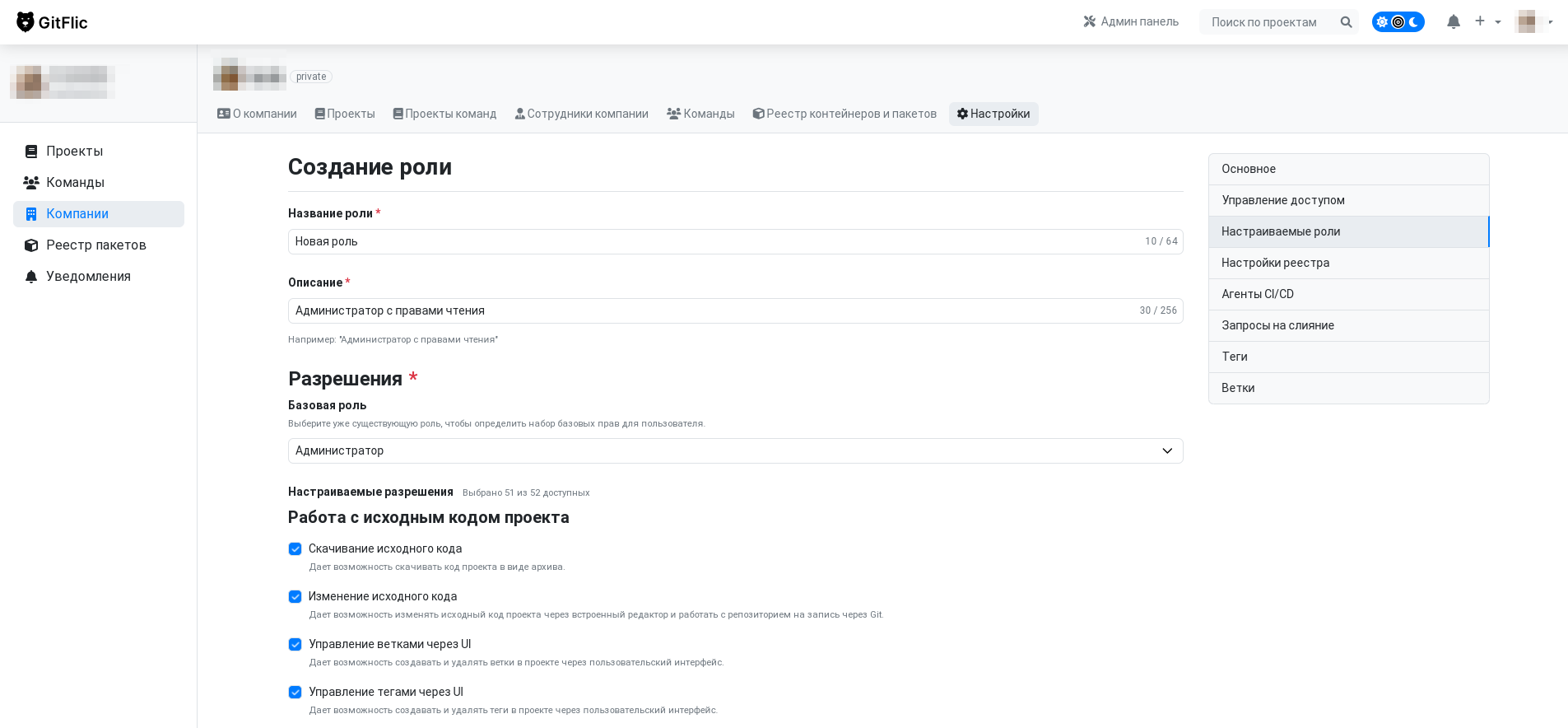
To create a custom role, specify its name, description, select a base role, and a set of permissions.
Effect of the Base Role
The selected base role affects certain permissions:
- Branch and tag protection — the specified base role must be equal to or higher than the role specified in the protection rules in order to access working with branches or tags covered by those rules.
- Inviting to a project — if a project participant has a custom role and the permission to manage access, they can invite other users to the project with a base role not higher than their own.
- Assigning as responsible — a project member with a custom role whose base role is Developer or higher can be assigned as responsible in the merge approval rules.
Nuances of Working with Custom Roles
The functionality for creating custom roles is quite extensive. The number of possible permission combinations is huge. Therefore, the GitFlic team recommends using existing base roles as a template when creating your own. Below are some combinations of permissions whose interaction may not be obvious:
- The Clear all pipeline logs function, found in the project settings in the CI/CD section, requires a combination of two permissions—Manage project CI/CD and Manage artifacts.
- For the Toggle auto-merge function to be available, the Execute merge requests permission is required.
Also note that it is not possible to transfer project ownership to a participant with a custom role, even if the base role is Owner.
Permissions Table for Project Member Base Roles
| User Action | Guest | Reporter | Developer | Administrator | Owner |
| Read source code | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Download source code | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Modify source code | ✔️ | ✔️ | ✔️ | ||
| Manage branches via UI | ✔️ | ✔️ | ✔️ | ||
| Manage tags via UI | ✔️ | ✔️ | ✔️ | ||
| View issues | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Create issues | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Edit issues | ✔️ | ✔️ | |||
| Manage issue status | ✔️ | ✔️ | ✔️ | ✔️ | |
| Delete issues | ✔️ | ✔️ | |||
| View issue discussions | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Participate in issue discussions | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Edit issue discussions | ✔️ | ✔️ | |||
| Delete issue discussions | ✔️ | ✔️ | |||
| View merge requests | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Create merge requests | ✔️ | ✔️ | ✔️ | ||
| Change merge request status | ✔️ | ✔️ | ✔️ | ||
| Edit merge requests | ✔️ | ✔️ | |||
| Execute merge requests | ✔️ | ✔️ | ✔️ | ||
| Toggle auto-merge | ✔️ | ✔️ | ✔️ | ||
| View merge request discussions | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Create merge request discussions | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Close merge request discussions | ✔️ | ✔️ | ✔️ | ||
| Delete merge request discussions | ✔️ | ✔️ | |||
| View CI/CD | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Run CI/CD | ✔️ | ✔️ | ✔️ | ||
| Delete pipelines | ✔️ | ✔️ | |||
| Manage artifacts | ✔️ | ✔️ | ✔️ | ||
| Clear agent cache | ✔️ | ✔️ | |||
| Manage pipeline schedulers | ✔️ | ✔️ | |||
| View vulnerabilities | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Manage vulnerabilities | ✔️ | ✔️ | |||
| View releases | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Manage releases | ✔️ | ✔️ | ✔️ | ||
| View packages | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Creation packages | ✔️ | ✔️ | ✔️ | ||
| Deletion packages | ✔️ | ✔️ | ✔️ | ||
| Creation repository | ✔️ | ✔️ | |||
| Deletion repository | ✔️ | ✔️ | |||
| Create project wiki | ✔️ | ✔️ | |||
| Create project book | ✔️ | ✔️ | |||
| Manage basic project settings | ✔️ | ✔️ | |||
| Transfer project | ✔️ | ||||
| Delete project | ✔️ | ||||
| Manage project labels | ✔️ | ✔️ | |||
| Manage project access | ✔️ | ✔️ | |||
| Manage merge request settings | ✔️ | ✔️ | |||
| Manage tag settings | ✔️ | ✔️ | |||
| Manage branch settings | ✔️ | ✔️ | |||
| Manage project webhooks | ✔️ | ✔️ | |||
| Manage deployment tokens | ✔️ | ✔️ | |||
| Manage project CI/CD | ✔️ | ✔️ | |||
| Manage project CI/CD agents | ✔️ | ✔️ | |||
| Manage Jira integration | ✔️ | ✔️ | |||
| Manage Telegram integration | ✔️ | ✔️ | |||
| Manage email notification settings | ✔️ | ✔️ | |||
| Manage project package registry settings | ✔️ | ✔️ | |||
| View Git LFS storage in project settings | ✔️ | ✔️ | |||
| Manage project push rules | ✔️ | ✔️ | |||
| Manage custom scripts | ✔️ | ✔️ | |||
| Manage script variables | ✔️ | ✔️ |
Permissions Available to All Users
For a public project, there is a list of actions that can be performed by users who are not members of the project or have a custom role prohibiting such actions. Some of them do not require authorization. The list of such actions is below:
- Download source code (authorization requirement depends on service settings)
- Read source code via git clone/pull/fetch (authorization requirement depends on service settings)
- Read source code through the interface (authorization not required)
- View issues (authorization not required)
- Create issues (authorization required)
- View issue discussions (authorization not required)
- Participate in issue discussions (authorization required)
- View merge requests (authorization not required)
- View merge request discussions (authorization not required)
- Create merge request discussions (authorization required)
- View vulnerabilities (authorization not required)
- View CI/CD (authorization not required)
- View releases (authorization not required)
- Download release files (authorization requirement depends on service settings)
- View packages (authorization not required)
- Download package files (authorization requirement depends on project settings)
Permissions Table for Company Member Roles
| User Action | Guest | Reporter | Developer | Administrator |
| View public company projects* | ✔️ | ✔️ | ✔️ | ✔️ |
| Create projects on behalf of the company | ✔️ | |||
| View public projects of company teams | ✔️ | ✔️ | ✔️ | ✔️ |
| View company members | ✔️ | ✔️ | ✔️ | ✔️ |
| View teams in the company | ✔️ | ✔️ | ✔️ | ✔️ |
| Add new teams to the company | ✔️ | |||
| View packages | ✔️ | ✔️ | ✔️ | ✔️ |
| Creation packages | ✔️ | ✔️ | ||
| Deletion packages | ✔️ | ✔️ | ||
| Creation repository | ✔️ | |||
| Deletion repository | ✔️ | |||
| Manage basic company settings | ✔️ | |||
| Transfer company | ✔️ | |||
| Access to payment page and change plan | ✔️ | |||
| Manage company access | ✔️ | |||
| Create custom roles in the company | ✔️ | |||
| Manage company package registry settings | ✔️ | |||
| Manage company CI/CD agents | ✔️ | |||
| Manage company merge request settings templates | ✔️ | |||
| Manage company tag protection templates | ✔️ | |||
| Manage company branch protection templates | ✔️ |
Role Inheritance in Company Projects.
In company projects, a user only inherits the administrator role. Inheritance occurs when the user is not added directly to the project. For other roles, a separate access must be granted in the project settings.
Permissions Table for Team Member Roles
| User Action | Guest | Reporter | Developer | Administrator |
| View public team projects | ✔️ | ✔️ | ✔️ | ✔️ |
| Create projects on behalf of the team | ✔️ | |||
| View team members | ✔️ | ✔️ | ✔️ | ✔️ |
| Manage basic team settings | ✔️ | |||
| Transfer team | ✔️ | |||
| Manage team access | ✔️ | |||
| Manage team merge request settings templates | ✔️ | |||
| Manage team tag protection templates | ✔️ | |||
| Manage team branch protection templates | ✔️ |
Role Inheritance in Team Projects.
In team projects, a user only inherits the administrator role. Inheritance occurs when the user is not added directly to the project. For other roles, a separate access must be granted in the project settings.
Automated translation!
This page was translated using automatic translation tools. The text may contain inaccuracies.