DAST
This feature is available in the Enterprise version
DAST - Dynamic Application Security Testing, a dynamic code security analyzer.
DAST Compatibility: Ensure your code analyzer supports SARIF-formatted reports.
Configuring DAST for a Project
DAST runs on agent resources. The code analyzer displays reports after executing the scenario specified in the .yaml file.
To enable DAST, you need to select and connect a dynamic analyzer to your project manually.
Working with DAST analyzer reports functions similarly to SAST reports. You must specify the path to the SARIF-formatted report artifact in the artifacts:reports parameter with the analyzer type set to dast. If you don't explicitly specify this parameter, the report will default to sast. To include multiple report files, specify each file path separately.
artifacts:
reports:
sast:
paths:
- sast_report.json
dast:
paths:
- dast_report.json
- dast_report_2.json
For more details on yaml file configuration, see this page
How It Works
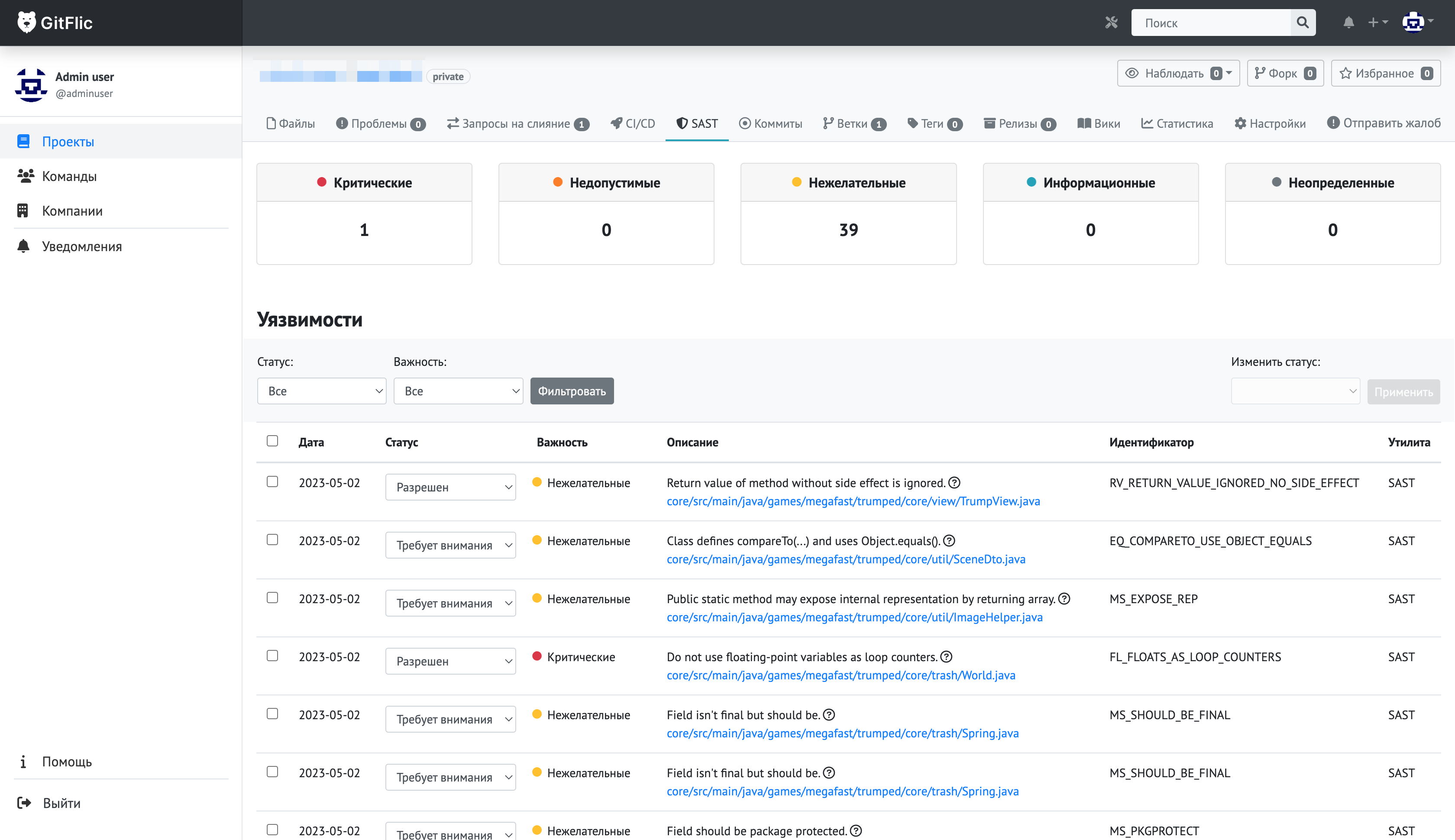
Static and dynamic code analyzers classify vulnerabilities into 5 severity levels:
- Critical
- High
- Medium
- Low
- Unknown
On the project's Security page, you can investigate vulnerabilities by filtering them by severity and status.
You can view detailed information for each vulnerability, including the file location, commit, and line number where it was detected, along with additional context.
Automatic Translation!
This page was automatically translated. The text may contain inaccuracies