SAST (Static Application Security Testing)
Available in Enterprise version
SAST (Static Application Security Testing) is a static code analyzer for security vulnerabilities.
Compatibility Note: Ensure your code analyzer supports SARIF-formatted reports.
Configuring SAST for Your Project
SAST runs on agent resources. The code analyzer displays a report after executing the script specified in the .yaml file.
To enable SAST:
1. Select and integrate a static analyzer into your project.
2. Ensure the analyzer outputs a JSON report in SARIF format.
3. Upload the report as an artifact with the reports parameter:
artifacts:
reports:
paths: 'core/target/spotbugsSarif.json' # Path to report file (multiple paths allowed)
base_dir: 'core/src/main/java' # Optional. Required if analyzer runs from a submodule.
For detailed .yaml configuration, refer to the GitFlic CI/CD Documentation.
How It Works
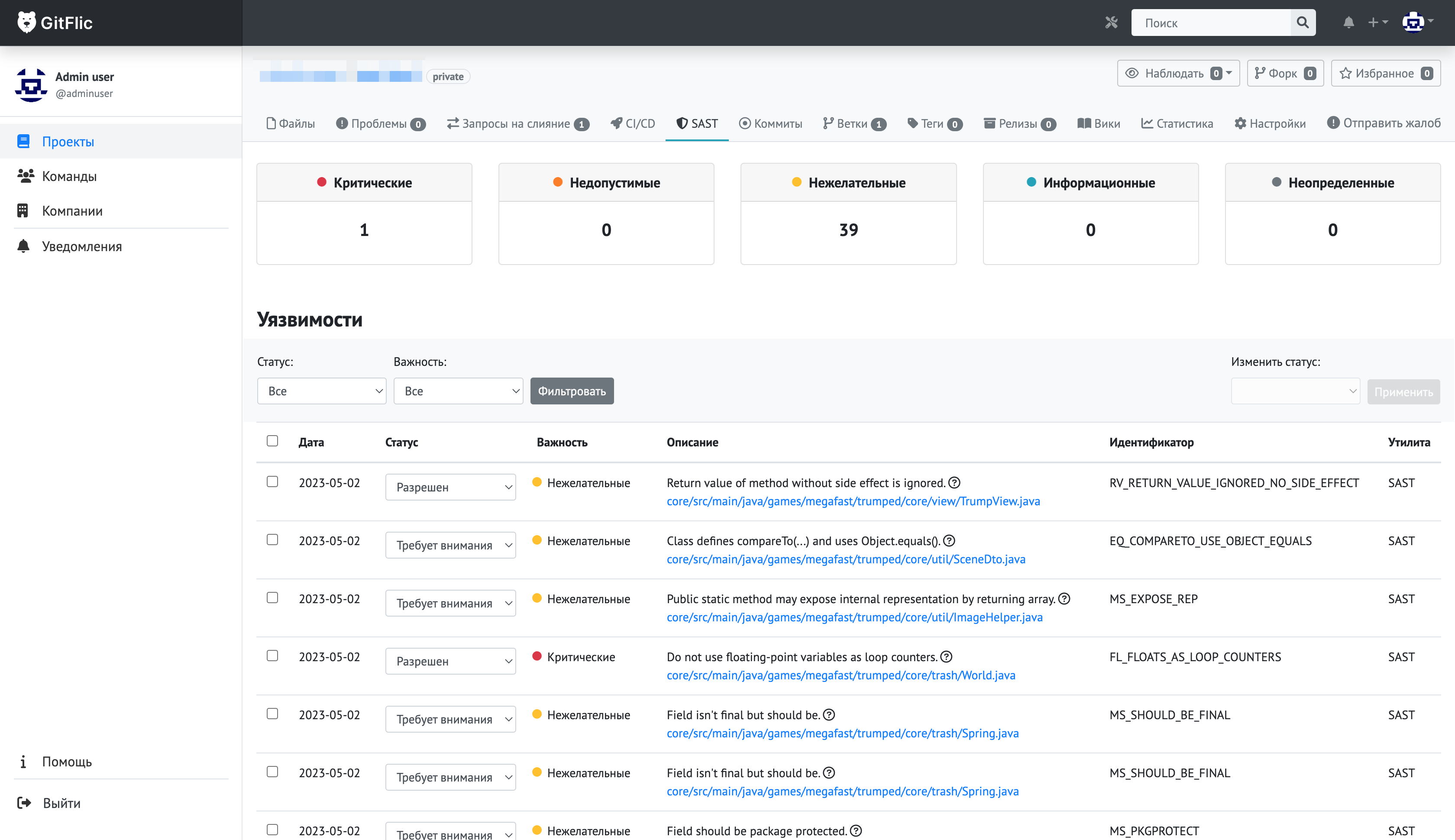
SAST categorizes vulnerabilities into 5 severity levels:
1. Critical
2. High
3. Medium
4. Low
5. Undefined
Viewing Results
- Navigate to Security > SAST in your project to filter vulnerabilities by severity and status.

- Click any vulnerability to see:
- File path, commit, and line number where detected.
- Detailed description and remediation guidance.

Automatic translation!
This page has been automatically translated. The text may contain inaccuracies